Optimum ISP is MITMing its customers
A Man In the Middle (MITM) attack is basically when an attacker stealthily interposes itself between you and another agent (person, server, etc), and intercepts and possibly alters the communication. Normally the bailiwick of cybercriminals or Advanced Persistent Threats and Nation-State Actors, turns out this is commonly done by our ISPs as well.
I was browsing the web this morning and visited this page about the CHERI project. That page is hosted on the University of Cambridge website and should be completely safe to visit.
However, when I loaded it up on my iPhone, I saw a banner from Optimum advertising their free upgrade to faster internet. (I believe this is known as a DOM injection attack.) I had a literal WTF moment as this should be impossible. The website is served over HTTPS which should mean that, unless someone has broken the crypto underling modern TLS, even my ISP, which sees all of my internet traffic, should be incapable of decrypting and modifying any of that traffic.
But what if that website loads some resources not via HTTPS? I opened up the debugger’s networking tab on a Firefox desktop browser window, loaded that site, and sure enough, there is a plain HTTP request to a single resource. (Oddly I am not able to reproduce this consistently, nor at all with Chrome.)
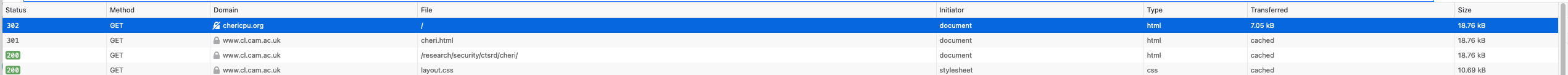
So what probably happened is
-
Optimum saw an unencrypted HTTP request
-
fingerprinted my request by IP address and perhaps some other mechanisms
-
determined that it had not already sent me that advertisement
-
injected some Javascript into the content of that request
-
the Javascript payload added a little banner at the top of the page I was viewing notifying me of the newer, faster internet speeds
When I got past the initial shock, I recalled that I had read about something like this before, and was able to track down a post from hackernews Xfinity is Man-in-the-Middle (MITM) Attacking my Internet from 2019. See also Comcast still uses MITM javascript injection to serve unwanted ads and messages from 2016.
This commenter on the Xfinity post purports to have knowledge of the details of how Comcast’s “User Messaging” feature works, via a network appliance that is operated by other ISPs as well. I’m unable to find any more information on the internet about what this appliance might be, who makes it, etc.
It isn’t hard to find software that does this sort of thing at the org/corporate level, e.g. Ivanti Traffic Manager can “decrypt and re-encrypt SSL traffic dynamically”, and there is probably a raft of Cisco hardware and software that can do the same things. But I haven’t been able to find anything specifically for ISPs that would support this functionality. The closest thing is this document on Cisco SD WAN technology that mentions that
An accepted packet is eligible to be modified by the additional parameters configured in the action portion of the policy configuration.
I would guess, however, that this is too “low level” an operation for the sort of functionality we’re talking about, and there is likely some kind of appliance dedicated to intercepting and modifying specifically HTTP traffic without worrying about modifying and reassembling individual packets.
But it seems equally plausible that it is just software running on the modem or router itself, which could periodically “phone home” to the ISP to check whether there are any “user messaging” campaign the ISP wants to run.
Unfortunately there probably are no ISPs (maybe Google Fiber?) whom you could trust to not engage in this sort of shady activity.
June 2025 update
When I was originally looking into this in 2023, I had a hard time discovering the names and details of off-the-shelf networking appliances that would implement this functionality for ISPs.
As a testament either (or probably both) to how shitty Google search had gotten even at that point, and how much better LLMs have gotten, I took up this question again using Claude Sonnet 4, and made much more progress. Claude broke these down into a number of different categories (e.g. “Deep Packet Inspection (DPI) Appliances” vs “Web Optimization and Content Modification Platforms” vs “Transparent Proxy Solutions”), but since there is significant overlap between them I’m not sure that is very useful or accurate.
The most basic job of networking appliances like routers is to direct packets (I’ll refer to the conents of this traffic as “packets” for now even though that isn’t strictly accurate for all networking technologies) from their source to their destination.
To do this, they typically need to just look at the headers, which are typically a small part of the overall packet, describing source and destination addresses and ports, TTLs, and other metadata.
When networking appliances look into the packets beyond just the headers, that is called Deep Packet Inspection. On its own, it does not involve modifying that data, or changing behaviour based on packet contents, but it is an essential part of technologies that do so.
The following is a short list of companies and services that offer or have offered functionality capable of or necessary for the sort of DOM injection attack mentioned above.
Sandvine
- Sandvine has developed networking appliances and software since they were formed in Waterloo Ontario in 2001.
- In 2017, Procera merged with Sandvine to be owned by private equity firm Francisco Partners. This Opinions on procera reddit post from ~2016 provides some colour on the services offered by Procera’s PacketLogic product, primarily discussing its use in traffic shaping. The bit about PacketLogic’s frequent traffic detection list updates is particularly interesting. The link to its changelog returns a 403 error, but you can access it via the wayback machine, last updated in 2020: PacketLogic traffic detection changelog. It could apparently distinguish traffic from Amazon Alexa, various VPNs, League of Legends, HBO Go, and so on. Given that much of this traffice was likely encrypted, I’m not sure how it was able to reliably identify it; presumably, it used a combination of IP and domain name lists, dest/source port mappings, and statistical/ML-based traffic analysis.
- This Sept 19 2024 press release mentions new ownership, injection of new capital, and refocus to “serving customers in large democratic markets”. It seems that the main motivation for this was that it was “bleeding money over its alleged deals with authoritarian regimes around the world and its inclusion on the U.S. Department of Commerce’s Entity List” according to this Nov 26, 2024 story from CTV. They apparently completed this restructuring on March 3, 2025, and “re-emerged” as AppLogic Networks, now a “software-only” company. See this 2018 report from Citizenlab on the use of Sandvine technology for spyware, malware, and adware in Turkey, Syria, and Egypt.
- It looks like as early as 2019 they had begun to see and discuss the challenges presented to their DPI technology by the increasing embrace of encrypted web traffic. This 2019 whitepaper, Encryption and DPI: Current and Future Services Impact (PDF) generally paints the move to increased encryption in a positive light…
One of the clear benefits that a widespread usage of encryption brings is the elimination of some of the use cases that have driven a negative perception of DPI. Use cases that involve session metadata gathering or even URL-based intelligence can no longer gather potentially sensitive user information. It’s no longer a case of what is desired by the operator or regualtory bodies - the use cases are simply not possible.
We believe that this elimination of the negative use cases will have a positive impact on the DPI market as a whole. We also believe that the position taken by security researchers - to see any middleware as a possible attacker on the network - is an accurate one. User privacy is better dictated by something under the control of the user - the operating system and browser - than by something under the control of the operator - the middlebox
- …though the wikipedia entry on the use of Sandvine technology in disabling internet access during the 2020-1 Belarusian protests makes it fairly plain that their chief interest was not protecting consumer privacy or freedom of information.
- The most detailed information I could find on their older product offerings was this slide deck, Introduction to Sandvine DPI. It is not clear what year it’s from, and it doesn’t explicitly mention anything that would allow the sort of DOM injection behaviour that initially piqued my curiousity, but from the Citizenlab reporting it seems reasonable to infer that they a) had this capability at least at some point in the past, b) had deployed it at least in the middle-east, if not elsewhere, and c) are not keen to discuss it publicly.
NebuAd
Now defunct, this is basically a perfect example of the sort of technology ISPs were using to do content injection. The NebuAd wikipedia page gives a good overview that I will not attempt to summarize.
Cisco Service Control Engine
As with basically all of these “solutions” it’s hard to tell from the documentation what exactlyt this does, how it work, and what prerequisites it has (e.g. does it require a root cert to be installed on endpoints? Almost certainly not if it is intended for consumer ISP use).
But the SCE documentation suggests it can do:
- DPI
- per-subscribed application monitoring, e.g. determining who is using “over-the-top (OTT) voice or how much bandwidth is being used by high-use subscribers”
- Content Filtering and Parental Control: unclear how reliable this is given encrypted web traffic, but it could be just based on domain name which still must be sent over the network unencrypted for most cases (DNS resolution and TLS SNI).
- Advertising: Behavioral Targeting
- No mention of anything like content injection