Hollywood hacking with JSON Bourne (2016)
Warning, plot spoilers ahead.
This movie is of fairly mixed quality, in my opinion. It isn’t bad, yet doesn’t quite live up to the quality of the original three. It isn’t easy to put my finger on what the issue is, there are good performances by great actors, enough thrilling action scenes. Certainly some of the dialogue is hackneyed and stilted, especially for some reason in the scenes involving Deep Dream CEO Aaron Kalloor.
In any case, this piece is not about that, we’re just having some fun picking apart the scenes involving computers and software.
The film starts off strong, in some sort of hacker’s den in Reykjavík, where ex-Treadstone agent Nicky Parsons is attempting to hack into CIA computers to obtain information on their blackops programs. As Nicky walks through the dark industrial space, dimly illuminated by electronics, we catch a glimpse of some cyberpunk-esque characters apparently attacking a Japanese Bank, one of them suggesting that the other “Use SQL to corrupt their databases…”
This was one of my favourite moments. It is so perfectly “just barely wrong” and hard to put your finger on exactly what’s off.
You definitely do use SQL to interact with basically all traditional databases, in fact, SQL is so strongly tied to databases that this is almost a bit like saying “use healing to cure the patient”, or telling a mechanic to “use wrenches to fix the engine”. I’m sure at some point with some database it has been possible to cause corruption by triggering a bug with a specially crafted SQL statement, but telling someone “use SQL to corrupt their database” gives no concrete information on how to do this, or what to do next.
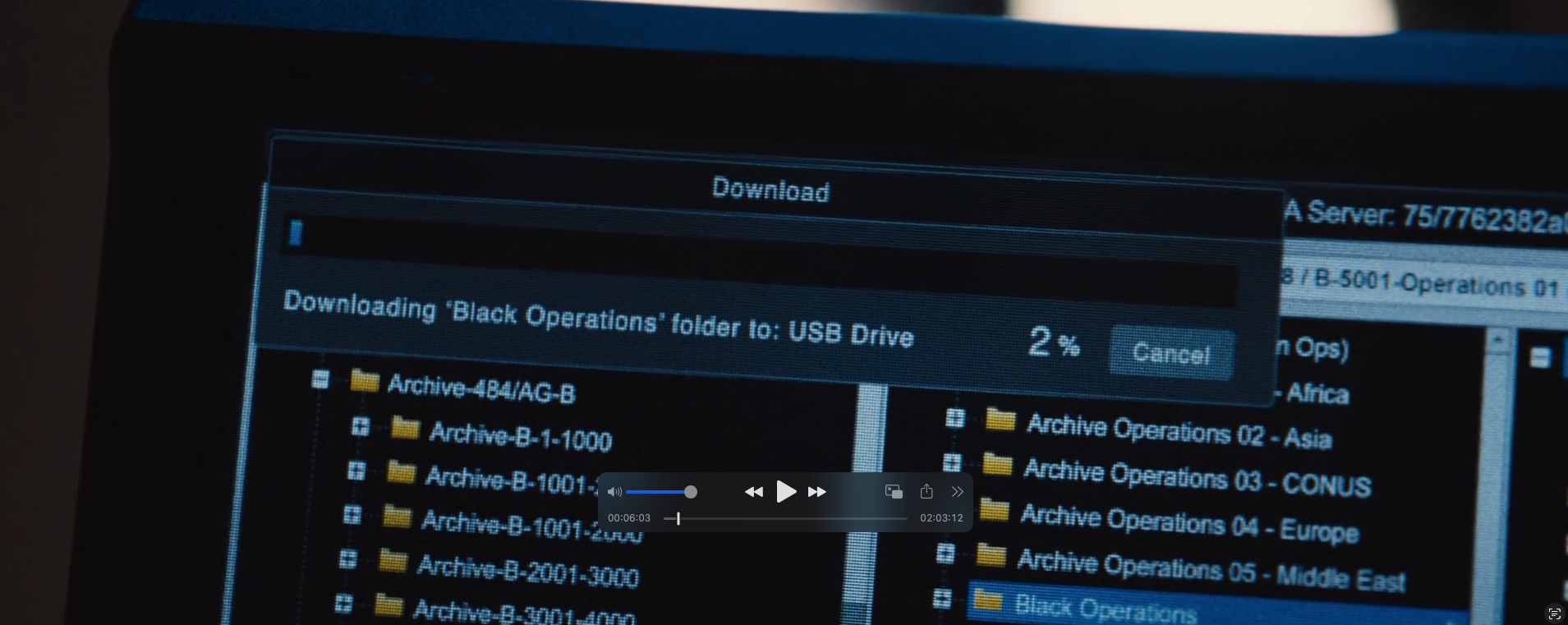
Next we are treated to this visual as Nicky begins the download. We are to imagine that someone had the 200 IQ idea of having a folder titled “Black Operations”. I guess they already had a folder called “Secret Evil Stuff” so they couldn’t use that. On the other hand, it is entirely possible that the Venn diagram of midlevel bureaucrats ∧ people running semi-legal shadowy intelligence operations would result in someone who titles their folders in this way.
One of my favourite aspects of these scenes is getting to imagine the software development process that went into this.
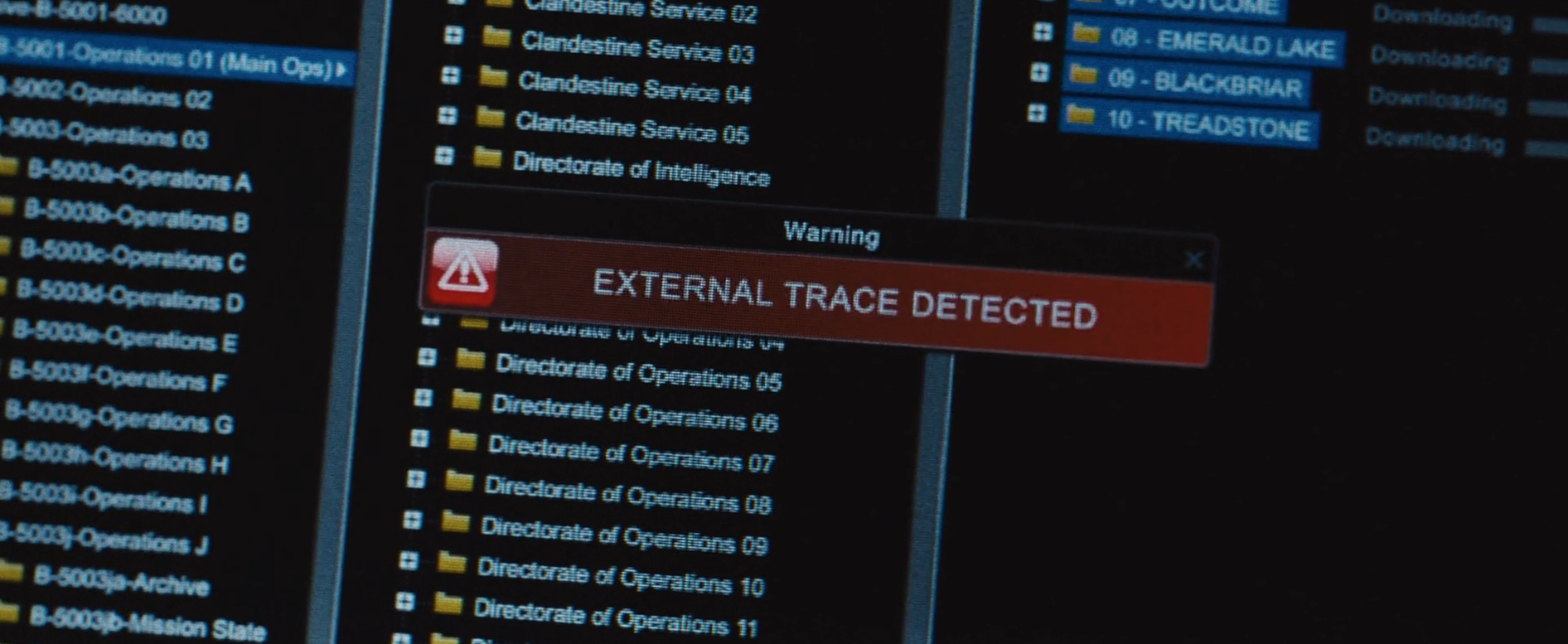
Manager: So this meeting is to discuss the external trace detector functionality that we’re going to need.
Network Engineer: External trace detector? What… what does that even mean? Is that supposed to mean like whether we can detect if someone is passively sniffing our network traffic? But if someone is “tracing” us cuz they have control of a router on one of the dozens of network hops between our machine and whatever other machine it’s talking to, how can we possibly know that?
Manager: …When we detect an external trace you have to show a dialog that says “External Trace Detected” and make sure you use the red alert icon.
UI Engineer: Should we use the old icon set with the gradients, or the new flat ones? Actually we might be able to just use an emoji if the system font supports it.
Other Software Engineer: Can we reuse some of the internal trace detector logic? I wrote a pretty cool plugin system for that component and I think this would be a good candidate for a plugin architecture.
UI Engineer: Oh yeah, what if we also detect an internal trace at the same time? And what if there are multiple internal/external traces? The number of possible concurrent external traces is theoretically unbounded. This is actually a good opportunity to finish the multi-modal notification queue manager we’ve been trying to launch. We could just queue up however many notifications of internal/external traces and then the user will dismiss them before proceeding. And if there are too many queued up, for example because there is a sudden and ongoing influx of new external/internal traces, the notification queue can support deferring notifications until later and also supports intelligent notification deduplication and also batch notification dismissal. We really will not be able to build this functionality without completing the multi-modal notification queue manager.
Manager: Listen we don’t have time for any of that, we just need the external trace detected popup ASAP, we are expecting a lot of external traces soon and this takes priority over other alerts and traces.
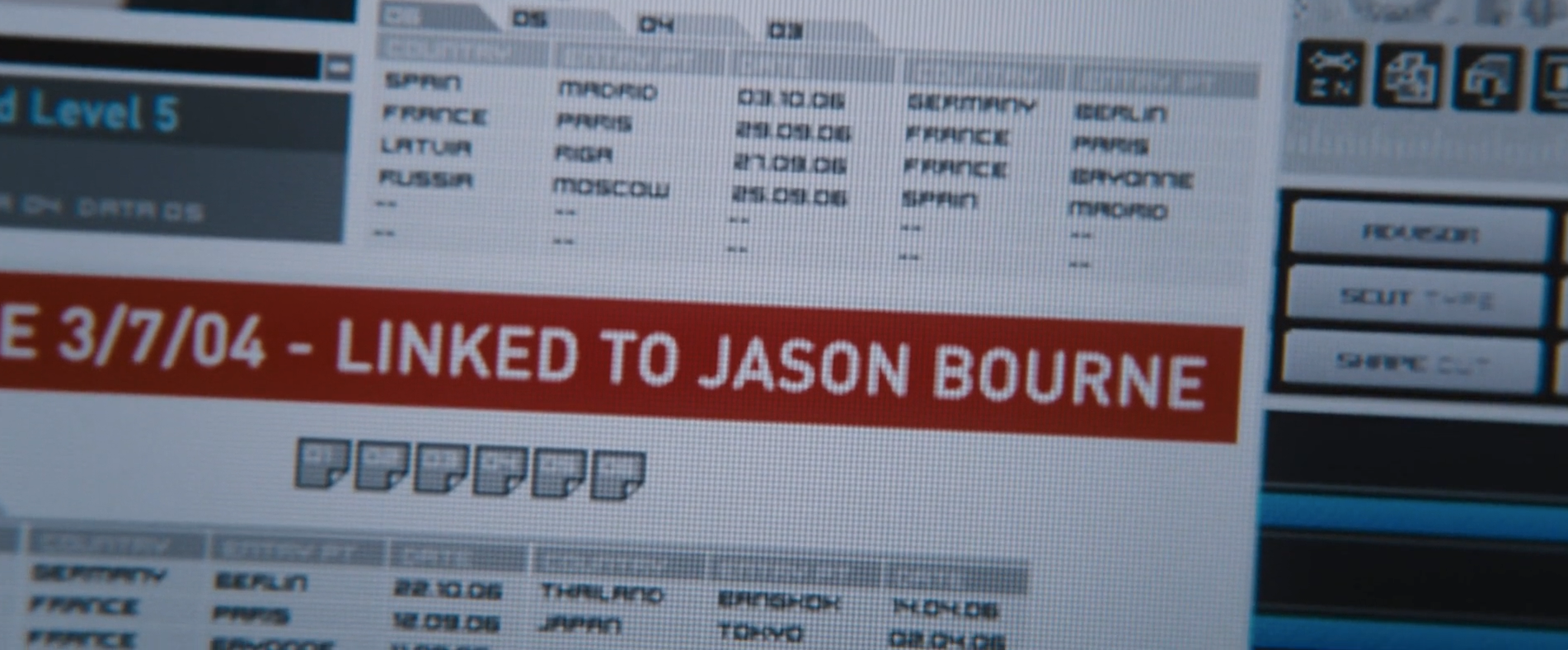
When someone views a file of someone else and that person has a link to Jason Bourne.
Manager1: Okay we’re going to need to add a “Jason Bourne link alert” to the page where we show information about anyone.
Engineer1: Wait, anyone?
Manager1: Yes anyone, Jason is our #1 target right now, and he could be linked to anyone, so it has to be shown on anyone’s page.
Engineer: There are at least 20 different systems we have for showing information about people, and our team only has access to 17 of them. Most of those systems don’t have clearance to access Jason’s file, so we’re going to have to create dummy records with the same name and details, but we’ll have to add a special flag to make sure they don’t trigger leak detection protocols that determine when systems with lower clearance inadvertently somehow acquire data they shouldn’t have. This is going to take about 2 maybe 3 years.
Manager1: (Stares blankly for several seconds contemplating the vastness of the universe.) Well let’s at least get it into MANHUNT and OverwatchV2 and OverwatchV3.
Manager2: MANHUNT has a feature freeze right now, we’re moving to an event sourcing system and that is our #1 priority, we won’t be able to add this alert until next quarter at the earliest. OverwatchV3 probably has clearance to get the Bourne data file but OverwatchV2 doesn’t and is in maintenance mode to discourage people from continuing to rely on it, so we won’t be able to add it there at all, but people really shouldn’t be using it anyway… so it should be okay.
UI Engineer: We already have the “Bram Kotke link alert” in MANHUNT and that takes up all remaining screen height on the profile of anyone who is linked to him, which means that we can’t have both it AND the “Jason Bourne link alert” on the same screen, cuz all the Europe terminals have scrolling disabled.
Manager1: Who the fuck is “Bram Kotke”?
Manager3: You aren’t cleared to know that. Just put them side by side and make the font smaller.
Manager1: No, we need the Bourne alert to be bigger and redder, it has to pop.
Manager3: The Bram alert is higher priority, take it up with the Director if you have a problem with that.
Engineer2: If they have multiple links to Bourne, do we show the date of the first one or the most recent one?
Engineer1: Also TopTrail will default to showing Bourne’s name prior to his entry into Treadstone since you don’t have the ability to overwrite names, only add aliases, so in TopTrail it will have to show “Linked to David Webb”.
Manager1: You’ll have to show the alias then, no one knows who David Webb is.
Engineer1: There’s no way to show just a single alias though, it will have to show all aliases. That rule was implemented after the SIREN fiasco in ‘18 when we missed her because TopTrail wasn’t showing all the aliases, you had to click to expand and people usually didn’t do that.
UI Engineer: That’s going to overflow the Europe terminals’ viewports, it’ll push all the other information off screen.
Manager1: I don’t care what you have to do, just fucking show “Jason Bourne link alert” if the person was ever linked to Jason Bourne.
Engineer2: “Linked” is fairly nebulous though, like isn’t everyone who worked on Treadstone at all linked to him? Arguably we are linked to him now by virtue of working on this project. Can you define “linked” and also whether it is only 1st or also 2nd, 3rd, nth-degree linkages?
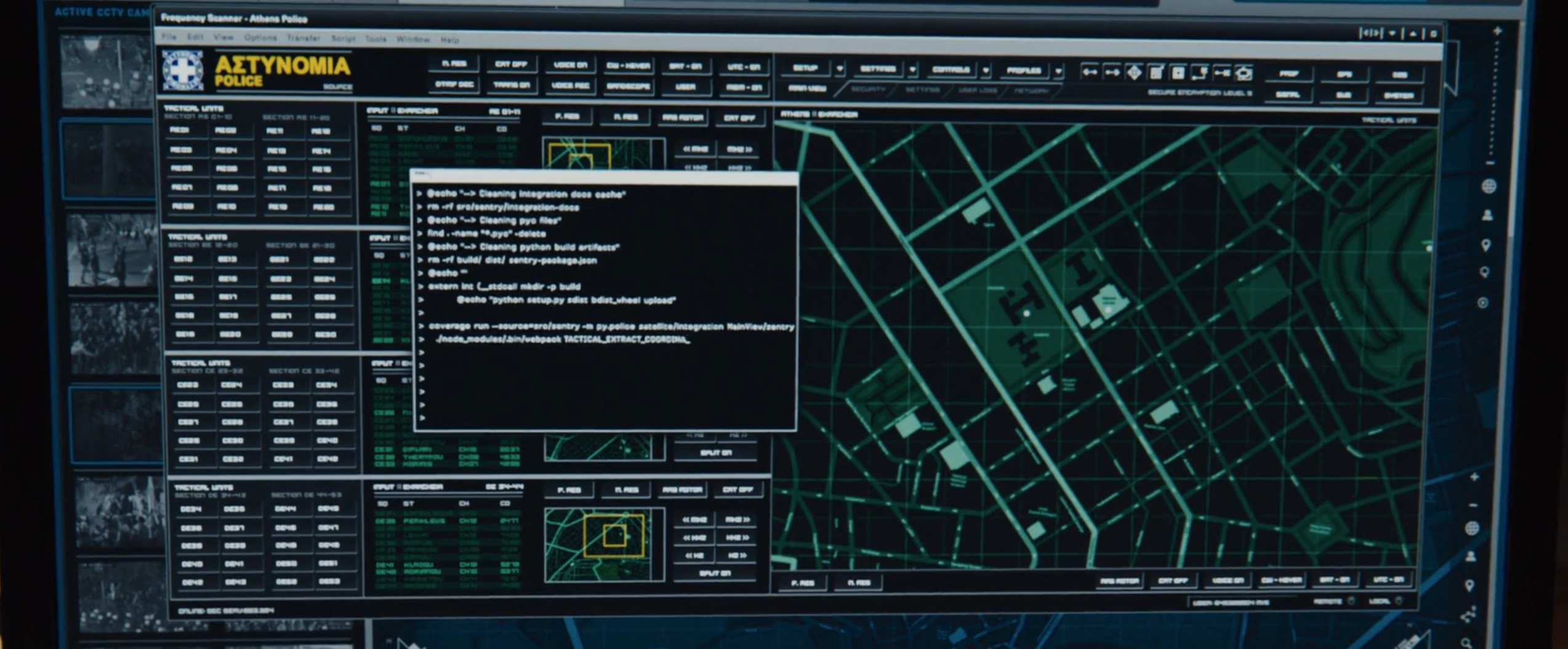
This next one I just enjoyed because this urgent hacking task also involved a few “clean up build artifacts” steps.
This line of USB sticks is for encrypted data only.
I liked this little easter-egg-ish touch. WGET is not a crime though it is a bit hard to believe that the CIA lets their agents put fun stickers on company laptops.
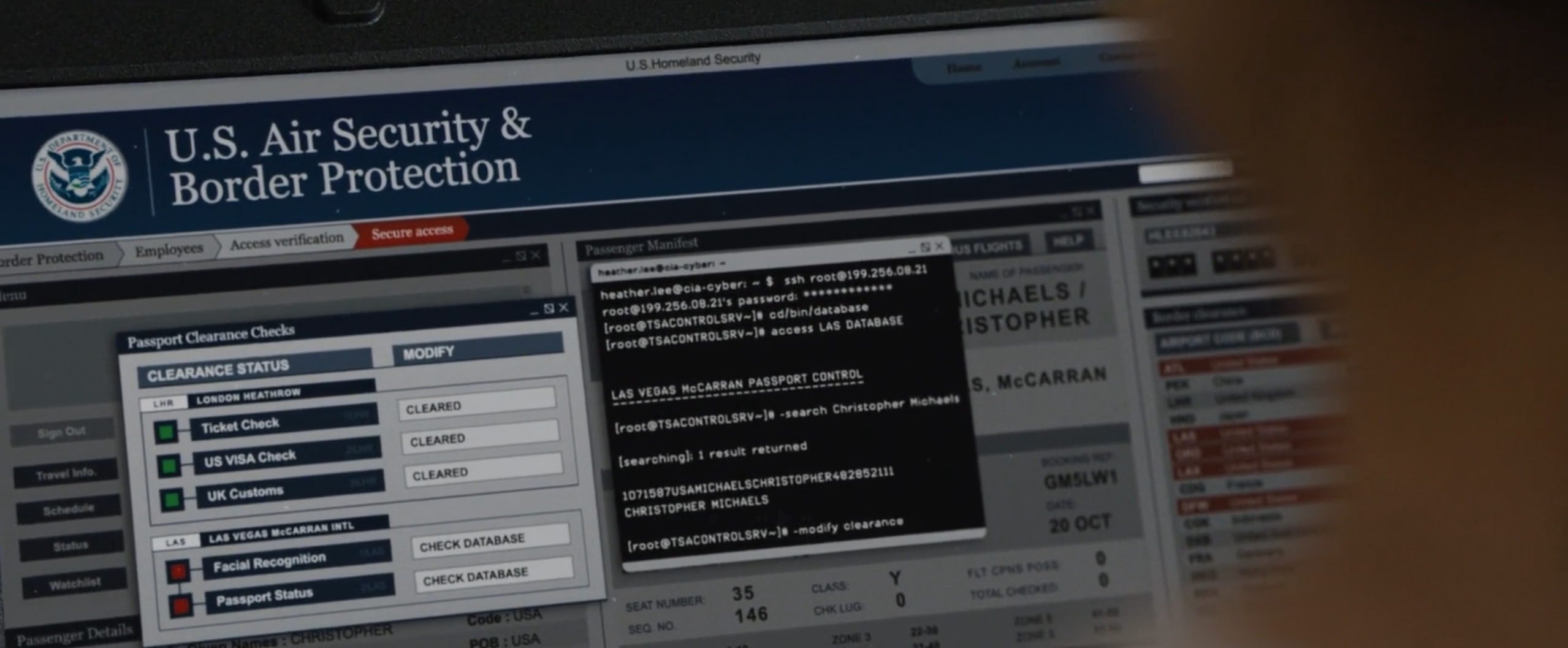
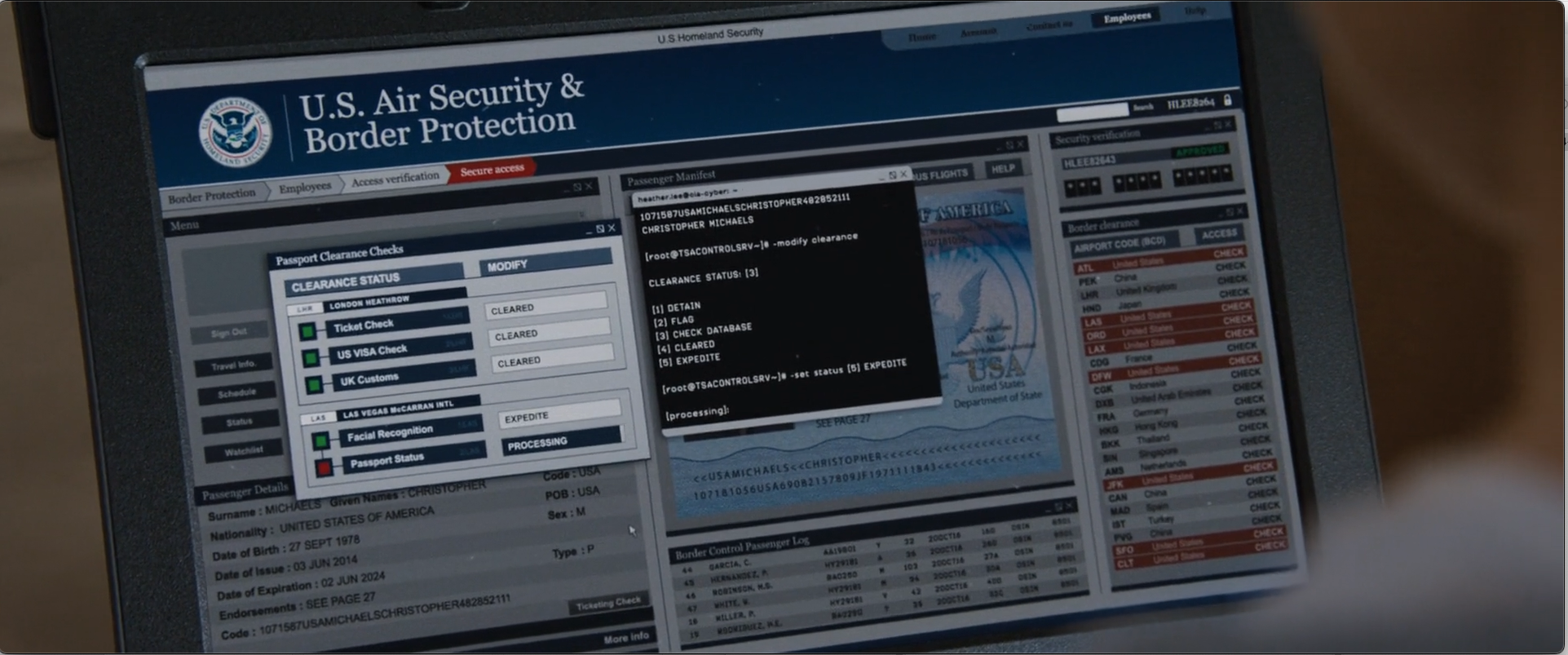
Agent Heather Lee helps Bourne get through an ID check at an airport.
cd/bin/databaseseems like a mistype ofcd bin/database. I guess there could be a folder calleddatabasein the user’sbinfolder and it could have a tool calledaccesswhich takes a database name.- I’ve never seen a database that allows you to search in this way, especially without specifying what columns or fields you want to look in. I guess this is some kind of futuristic smart database that just knows how to translate your natural language question into whatever query language it uses under the hood.
I wish there were a term for the phenomenon on display in this film, which is roughly: writer with lack of familiarity with some domain of technical expertise produces a facsimile that is close enough to pass muster with lay audiences but comes across as clumsy if not ludicrous to people with some knowledge of the field.
I use “technical expertise” quite broadly, it could encompass painting technique, meteorology, even things that I would consider to be quackery, e.g. you could have a portrayal of a homeopathic healer that gets all the details slightly wrong and ends up appearing absurd to those with knowledge of homeopathy.
I also wonder what the earliest instances of this might be. Shelley’s Frankenstein comes to mind as a counter-example. It’s been a long time since I read that book, but I don’t believe she dwells much at all on the biological/scientific aspects of reanimation, perhaps having Dr. Frankenstein claim that he is leaving details out precisely to avoid copycats. Maybe this wasn’t really much of an issue until the 20th century since prior to that it was possible to be both an accomplished author of fiction and relatively well-versed in the details of various sciences, since the breadth and depth of scientific knowledge was so much more limited then (Diderot, for example, the great encyclopedist and author of various works of fiction).
In Doyle’s Holmes pieces, moving from the early to late 19th century, there is every now and then a smattering of science but it’s fairly light, and even the bits that we would now call pseudo-science (e.g. physiognomy of the criminal face and head structure) would probably have been considered fairly accurate by the physiognomists of the time.
Perhaps one of the earliest instances of this could be Jules Verne’s “From the Earth to the Moon” (1865). I haven’t read it, but apparently he proposes launching astronauts to the moon using a giant cannon. Maybe some people had a good chuckle at the expense of that idea, though even that doesn’t seem to quite fit what I’m struggling to describe here, since arguably the implausibility and foolishness of blasting someone to the moon with a cannon should have been obvious to even non-experts back then if they took a moment to consider the immense physical stress that would place upon the human body.
As usual I have no conclusion, that’s it.